Everybody nowadays is working remotely in different kinds of areas of the organisation which is the main reason that different kinds of attempts are made by the concerned people for different kinds of sources for different kinds of tools which they are using. All of these activities are normally unavoidable and ultimately will be coming to the forefront for the business organisations to function very smoothly. So, having a good understanding of the credentials in the form of username as well as password is a great idea so that things will be kept in a perfect table in a database without any kind of issues and ultimately there will be no chance of any kind of problem.
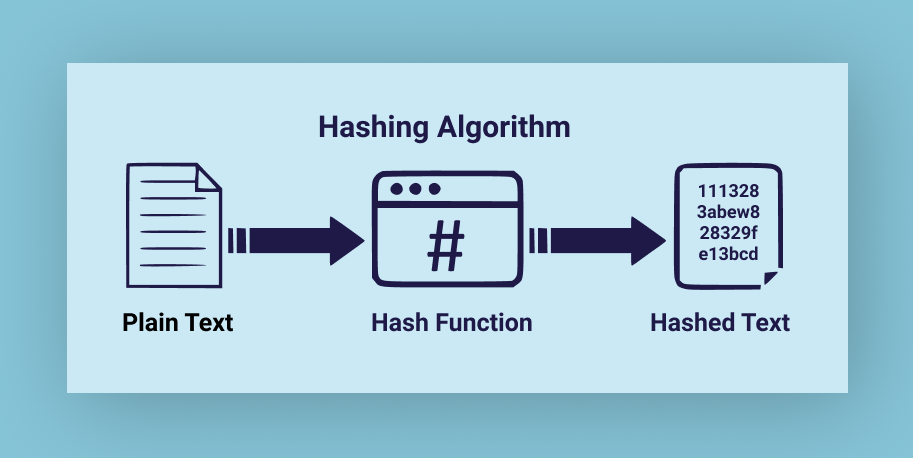
Understanding the technicalities of hashing algorithms is definitely important because this is a fundamental component of the cryptography strategy of organisations which very well means chopping the data into smaller and mixed-up pieces and ultimately letting it go back to the original state without any kind of doubt. Hashing algorithms in this particular case will be helpful in generating the fixed length result of the hashing value which will be helpful in providing people with a good understanding of things without any kind of doubt. Basically, this will be very much supportive in terms of ensuring the security of the password and also helps in making sure that storage will be carried out in proper pairs so that the user’s name and database table will be understood without any kind of hassle throughout the process.
Some of the basic features to be taken into consideration at the time of choosing the best possible type of function associated with hashing algorithms have been explained as follows:
- It should behave as a one-way function: One of the major benefits of the implementation of the right kind of hashing algorithms is that it will be significantly focused in a single direction and will be acting as a one-way function. Having a good understanding of this particular system will be definitely helpful in ensuring that people will never be getting the initial inputs which will be leading to the result and ultimately things will be sorted out very easily. So, determining the right kind of things in this particular area is a great idea and ultimately focusing on the runway function is a good approach.
- Avalanche effect:Understanding the technicalities of the avalanche effect is also very much important in this particular case so that people will be able to deal with the particular output and input very successfully. Basically, if not paid attention to it will be leading to a rustic change in the output which is the main reason that having a good understanding of things is definitely important.
- Fast in terms of computation: Another very important thing to be taken into consideration by people at the time of introducing the hashing algorithms is to go for that particular option which is very fast in terms of competition so that generating the results within seconds will be done very easily and successfully. This will be helpful in making sure that things will be perfectly implemented very strongly and ultimately there is no chance of any kind of chaos throughout the process.
- There should not be any kind of collision: Another very important aspect to be taken into consideration in this particular case is to go for that particular system in which the output of two input parameters should never be the same. Basically, there should not be any kind of collusion or confusion in this particular case so that things are sorted out very easily and successfully.
- Deterministic: Having a good understanding of the technicalities of the concept of hashing algorithms is definitely modern irrespective of if people are checking it or not. This will be especially coming into hand whenever people will be requiring the things at the verified and different points in time without any kind of problem throughout the process.
What are the different types of hashing algorithms available in the industry?
- MD5: Introduction of this particular system is directly associated with a good opportunity for passwords which will be converted into a specific pattern with the help of this particular method. This will be very much nonsecure and ultimately will be based upon simply Google the value associated with it so that people will be able to enjoy easy accessibility to the original system
- SHA family of algorithms: This particular system was introduced in the year 1993 and has been compromised many times. So, focusing on a slightly improved version of this particular area is a great idea so that there is no chance of any kind of problem and ultimately things will be getting very much concerned and serious about the element of security throughout the process.
- Whirlpool: This is a 512-bit hashing function which has been very well derived from the advanced encryption standard in the whole process of getting things done very easily.
- RIPEMD family of algorithms: this will be standing for the RACE integrity primitives evaluation message direct which was developed in the mid-1990s ultimately people need to have a good understanding of the output length and input length in this particular case so that coverage will be understood very successfully. Dealing with the subsequent version of this particular area is definitely a great idea to avoid any kind of problem in the whole process.
- CRC32: This particular system is known as the cycling redundancy code and is very much common for the spreading properties in the whole process so that everyone will be able to enjoy the smooth transferring and validation without any kind of problem in the whole system
In addition to the above-mentioned points having a good understanding of the basic working of the concept of hashing algorithms is definitely important and ultimately depending on the exports from the house of Appsealing is a good approach so that people will be able to implement the things very successfully and proficiently right from the very beginning.